・2018/08/24
 Raspberry Piで CPUの脆弱性 Spectreと Meltdownの脆弱性をチェックする方法
Raspberry Piで CPUの脆弱性 Spectreと Meltdownの脆弱性をチェックする方法
(ラズパイで 2018年初頭に大騒ぎになったスペクターとメルトダウンの CPUの脆弱性をチェックする方法)
Tags: [Raspberry Pi], [電子工作]
● Raspberry Piで Spectreと Meltdownの脆弱性をチェックする方法
Raspberry Piで 2018年 1月に大騒ぎになった CPUの脆弱性 Spectreと Meltdownの脆弱性をチェックする方法です。
●今回動かした Raspberry Pi Raspbian OSのバージョン
RASPBIAN STRETCH WITH DESKTOP
Version:June 2018
Release date: 2018-06-27
Kernel version: 4.14
pi@raspberrypi:~/pytorch $ uname -a
Linux raspberrypi 4.14.50-v7+ #1122 SMP Tue Jun 19 12:26:26 BST 2018 armv7l GNU/Linux
● Raspberry Piで Spectreと Meltdownの脆弱性をチェックする方法
speed47/spectre-meltdown-checker
Spectre & Meltdown vulnerability/mitigation checker for Linux
Spectre & Meltdown Checker
# お決まりの sudo apt-get updateで最新状態に更新する
sudo apt-get update
# Spectre and Meltdown Checkerをダウンロードする
cd
wget https://meltdown.ovh -O spectre-meltdown-checker.sh
# Spectre and Meltdown Checkerを実行する
chmod +x spectre-meltdown-checker.sh
sudo ./spectre-meltdown-checker.sh
● Raspberry Pi 3Bでの Spectre & Meltdown Checkerの実行結果
pi@raspberrypi:~ $ cat /proc/cpuinfo
processor : 0
model name : ARMv7 Processor rev 4 (v7l)
BogoMIPS : 76.80
Features : half thumb fastmult vfp edsp neon vfpv3 tls vfpv4 idiva idivt vfpd32 lpae evtstrm crc32
CPU implementer : 0x41
CPU architecture: 7
CPU variant : 0x0
CPU part : 0xd03
CPU revision : 4
processor : 1
model name : ARMv7 Processor rev 4 (v7l)
BogoMIPS : 76.80
Features : half thumb fastmult vfp edsp neon vfpv3 tls vfpv4 idiva idivt vfpd32 lpae evtstrm crc32
CPU implementer : 0x41
CPU architecture: 7
CPU variant : 0x0
CPU part : 0xd03
CPU revision : 4
processor : 2
model name : ARMv7 Processor rev 4 (v7l)
BogoMIPS : 76.80
Features : half thumb fastmult vfp edsp neon vfpv3 tls vfpv4 idiva idivt vfpd32 lpae evtstrm crc32
CPU implementer : 0x41
CPU architecture: 7
CPU variant : 0x0
CPU part : 0xd03
CPU revision : 4
processor : 3
model name : ARMv7 Processor rev 4 (v7l)
BogoMIPS : 76.80
Features : half thumb fastmult vfp edsp neon vfpv3 tls vfpv4 idiva idivt vfpd32 lpae evtstrm crc32
CPU implementer : 0x41
CPU architecture: 7
CPU variant : 0x0
CPU part : 0xd03
CPU revision : 4
Hardware : BCM2835
Revision : a22082
Serial : 00000000xxxxxxxx
pi@raspberrypi:~ $ wget https://meltdown.ovh -O spectre-meltdown-checker.sh
--2018-08-22 08:30:51-- https://meltdown.ovh/
Resolving meltdown.ovh (meltdown.ovh)... 87.98.135.28
Connecting to meltdown.ovh (meltdown.ovh)|87.98.135.28|:443... connected.
HTTP request sent, awaiting response... 302 Moved Temporarily
Location: https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh [following]
--2018-08-22 08:30:52-- https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 151.101.72.133
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|151.101.72.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 127398 (124K) [text/plain]
Saving to: ‘spectre-meltdown-checker.sh’
spectre-meltdown-ch 100%[===================>] 124.41K --.-KB/s in 0.06s
2018-08-22 08:30:53 (2.12 MB/s) - ‘spectre-meltdown-checker.sh’ saved [127398/127398]
pi@raspberrypi:~ $ chmod +x spectre-meltdown-checker.sh
pi@raspberrypi:~ $ sudo ./spectre-meltdown-checker.sh
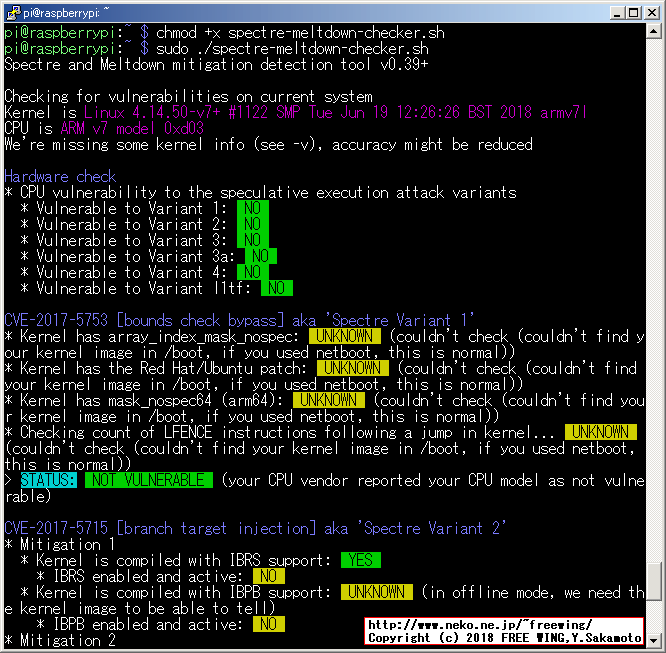
Spectre and Meltdown mitigation detection tool v0.39+
Checking for vulnerabilities on current system
Kernel is Linux 4.14.50-v7+ #1122 SMP Tue Jun 19 12:26:26 BST 2018 armv7l
CPU is ARM v7 model 0xd03
We're missing some kernel info (see -v), accuracy might be reduced
Hardware check
* CPU vulnerability to the speculative execution attack variants
* Vulnerable to Variant 1: NO
* Vulnerable to Variant 2: NO
* Vulnerable to Variant 3: NO
* Vulnerable to Variant 3a: NO
* Vulnerable to Variant 4: NO
* Vulnerable to Variant l1tf: NO
CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
* Kernel has array_index_mask_nospec: UNKNOWN (couldn't check (couldn't find your kernel image in /boot, if you used netboot, this is normal))
* Kernel has the Red Hat/Ubuntu patch: UNKNOWN (couldn't check (couldn't find your kernel image in /boot, if you used netboot, this is normal))
* Kernel has mask_nospec64 (arm64): UNKNOWN (couldn't check (couldn't find your kernel image in /boot, if you used netboot, this is normal))
* Checking count of LFENCE instructions following a jump in kernel... UNKNOWN (couldn't check (couldn't find your kernel image in /boot, if you used netboot, this is normal))
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2'
* Mitigation 1
* Kernel is compiled with IBRS support: YES
* IBRS enabled and active: NO
* Kernel is compiled with IBPB support: UNKNOWN (in offline mode, we need the kernel image to be able to tell)
* IBPB enabled and active: NO
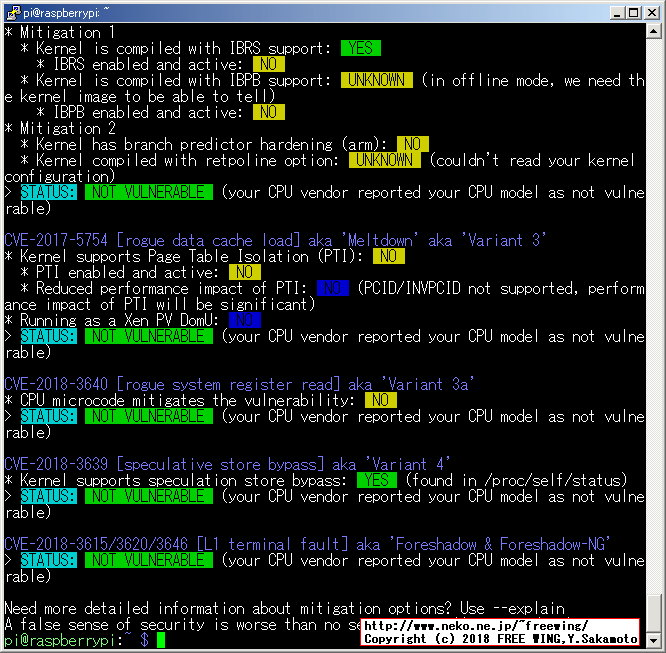
* Mitigation 2
* Kernel has branch predictor hardening (arm): NO
* Kernel compiled with retpoline option: UNKNOWN (couldn't read your kernel configuration)
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3'
* Kernel supports Page Table Isolation (PTI): NO
* PTI enabled and active: NO
* Reduced performance impact of PTI: NO (PCID/INVPCID not supported, performance impact of PTI will be significant)
* Running as a Xen PV DomU: NO
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3640 [rogue system register read] aka 'Variant 3a'
* CPU microcode mitigates the vulnerability: NO
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3639 [speculative store bypass] aka 'Variant 4'
* Kernel supports speculation store bypass: YES (found in /proc/self/status)
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3615/3620/3646 [L1 terminal fault] aka 'Foreshadow & Foreshadow-NG'
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
Need more detailed information about mitigation options? Use --explain
A false sense of security is worse than no security at all, see --disclaimer
● Raspberry Pi 3B+での Spectre & Meltdown Checkerの実行結果
Spectre and Meltdown mitigation detection tool v0.40
pi@raspberrypi:~ $ # Spectre and Meltdown Checkerを実行する
pi@raspberrypi:~ $ chmod +x spectre-meltdown-checker.sh
pi@raspberrypi:~ $ sudo ./spectre-meltdown-checker.sh
Spectre and Meltdown mitigation detection tool v0.40
Checking for vulnerabilities on current system
Kernel is Linux 4.14.98-v7+ #1200 SMP Tue Feb 12 20:27:48 GMT 2019 armv7l
CPU is ARM v7 model 0xd03
We're missing some kernel info (see -v), accuracy might be reduced
Hardware check
* CPU vulnerability to the speculative execution attack variants
* Vulnerable to CVE-2017-5753 (Spectre Variant 1, bounds check bypass): NO
* Vulnerable to CVE-2017-5715 (Spectre Variant 2, branch target injection): NO
* Vulnerable to CVE-2017-5754 (Variant 3, Meltdown, rogue data cache load): NO
* Vulnerable to CVE-2018-3640 (Variant 3a, rogue system register read): NO
* Vulnerable to CVE-2018-3639 (Variant 4, speculative store bypass): NO
* Vulnerable to CVE-2018-3615 (Foreshadow (SGX), L1 terminal fault): NO
* Vulnerable to CVE-2018-3620 (Foreshadow-NG (OS), L1 terminal fault): NO
* Vulnerable to CVE-2018-3646 (Foreshadow-NG (VMM), L1 terminal fault): NO
CVE-2017-5753 aka 'Spectre Variant 1, bounds check bypass'
* Kernel has array_index_mask_nospec: NO
* Kernel has the Red Hat/Ubuntu patch: NO
* Kernel has mask_nospec64 (arm64): NO
* Checking count of LFENCE instructions following a jump in kernel... NO (only 0 jump-then-lfence instructions found, should be >= 30 (heuristic))
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2017-5715 aka 'Spectre Variant 2, branch target injection'
* Mitigation 1
* Kernel is compiled with IBRS support: YES
* IBRS enabled and active: NO
* Kernel is compiled with IBPB support: NO
* IBPB enabled and active: NO
* Mitigation 2
* Kernel has branch predictor hardening (arm): NO
* Kernel compiled with retpoline option: UNKNOWN (couldn't read your kernel configuration)
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2017-5754 aka 'Variant 3, Meltdown, rogue data cache load'
* Kernel supports Page Table Isolation (PTI): NO
* PTI enabled and active: NO
* Reduced performance impact of PTI: NO (PCID/INVPCID not supported, performance impact of PTI will be significant)
* Running as a Xen PV DomU: NO
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3640 aka 'Variant 3a, rogue system register read'
* CPU microcode mitigates the vulnerability: NO
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3639 aka 'Variant 4, speculative store bypass'
* Kernel supports disabling speculative store bypass (SSB): YES (found in /proc/self/status)
* SSB mitigation is enabled and active: > STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3615 aka 'Foreshadow (SGX), L1 terminal fault'
* CPU microcode mitigates the vulnerability: N/A
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3620 aka 'Foreshadow-NG (OS), L1 terminal fault'
* Kernel supports PTE inversion: NO
* PTE inversion enabled and active: UNKNOWN (sysfs interface not available)
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3646 aka 'Foreshadow-NG (VMM), L1 terminal fault'
* This system is a host running a hypervisor: NO
* Mitigation 1 (KVM)
* EPT is disabled: N/A (the kvm_intel module is not loaded)
* Mitigation 2
* L1D flush is supported by kernel: NO
* L1D flush enabled: UNKNOWN (can't find or read /sys/devices/system/cpu/vulnerabilities/l1tf)
* Hardware-backed L1D flush supported: NO (flush will be done in software, this is slower)
* Hyper-Threading (SMT) is enabled: UNKNOWN
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
> SUMMARY: CVE-2017-5753:OK CVE-2017-5715:OK CVE-2017-5754:OK CVE-2018-3640:OK CVE-2018-3639:OK CVE-2018-3615:OK CVE-2018-3620:OK CVE-2018-3646:OK
We're missing some kernel info (see -v), accuracy might be reduced
Need more detailed information about mitigation options? Use --explain
A false sense of security is worse than no security at all, see --disclaimer
pi@raspberrypi:~ $ cat /proc/cpuinfo
processor : 0
model name : ARMv7 Processor rev 4 (v7l)
BogoMIPS : 38.40
Features : half thumb fastmult vfp edsp neon vfpv3 tls vfpv4 idiva idivt vfpd32 lpae evtstrm crc32
CPU implementer : 0x41
CPU architecture: 7
CPU variant : 0x0
CPU part : 0xd03
CPU revision : 4
processor : 1
model name : ARMv7 Processor rev 4 (v7l)
BogoMIPS : 38.40
Features : half thumb fastmult vfp edsp neon vfpv3 tls vfpv4 idiva idivt vfpd32 lpae evtstrm crc32
CPU implementer : 0x41
CPU architecture: 7
CPU variant : 0x0
CPU part : 0xd03
CPU revision : 4
processor : 2
model name : ARMv7 Processor rev 4 (v7l)
BogoMIPS : 38.40
Features : half thumb fastmult vfp edsp neon vfpv3 tls vfpv4 idiva idivt vfpd32 lpae evtstrm crc32
CPU implementer : 0x41
CPU architecture: 7
CPU variant : 0x0
CPU part : 0xd03
CPU revision : 4
processor : 3
model name : ARMv7 Processor rev 4 (v7l)
BogoMIPS : 38.40
Features : half thumb fastmult vfp edsp neon vfpv3 tls vfpv4 idiva idivt vfpd32 lpae evtstrm crc32
CPU implementer : 0x41
CPU architecture: 7
CPU variant : 0x0
CPU part : 0xd03
CPU revision : 4
Hardware : BCM2835
Revision : a020d3
Serial : 000000000xxxxxxx
Spectre and Meltdown mitigation detection tool v0.39+
pi@raspberrypi:~ $ wget https://meltdown.ovh -O spectre-meltdown-checker.sh
--2018-08-24 13:50:29-- https://meltdown.ovh/
Resolving meltdown.ovh (meltdown.ovh)... 87.98.135.28
Connecting to meltdown.ovh (meltdown.ovh)|87.98.135.28|:443... connected.
HTTP request sent, awaiting response... 302 Moved Temporarily
Location: https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh [following]
--2018-08-24 13:50:30-- https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 151.101.72.133
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|151.101.72.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 127398 (124K) [text/plain]
Saving to: ‘spectre-meltdown-checker.sh’
spectre-meltdown-ch 100%[===================>] 124.41K --.-KB/s in 0.03s
2018-08-24 13:50:31 (3.96 MB/s) - ‘spectre-meltdown-checker.sh’ saved [127398/127398]
pi@raspberrypi:~ $ chmod +x spectre-meltdown-checker.sh
pi@raspberrypi:~ $ sudo ./spectre-meltdown-checker.sh
Spectre and Meltdown mitigation detection tool v0.39+
Checking for vulnerabilities on current system
Kernel is Linux 4.14.50-v7+ #1122 SMP Tue Jun 19 12:26:26 BST 2018 armv7l
CPU is ARM v7 model 0xd03
We're missing some kernel info (see -v), accuracy might be reduced
Hardware check
* CPU vulnerability to the speculative execution attack variants
* Vulnerable to Variant 1: NO
* Vulnerable to Variant 2: NO
* Vulnerable to Variant 3: NO
* Vulnerable to Variant 3a: NO
* Vulnerable to Variant 4: NO
* Vulnerable to Variant l1tf: NO
CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
* Kernel has array_index_mask_nospec: UNKNOWN (couldn't check (couldn't find your kernel image in /boot, if you used netboot, this is normal))
* Kernel has the Red Hat/Ubuntu patch: UNKNOWN (couldn't check (couldn't find your kernel image in /boot, if you used netboot, this is normal))
* Kernel has mask_nospec64 (arm64): UNKNOWN (couldn't check (couldn't find your kernel image in /boot, if you used netboot, this is normal))
* Checking count of LFENCE instructions following a jump in kernel... UNKNOWN (couldn't check (couldn't find your kernel image in /boot, if you used netboot, this is normal))
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2'
* Mitigation 1
* Kernel is compiled with IBRS support: YES
* IBRS enabled and active: NO
* Kernel is compiled with IBPB support: UNKNOWN (in offline mode, we need the kernel image to be able to tell)
* IBPB enabled and active: NO
* Mitigation 2
* Kernel has branch predictor hardening (arm): NO
* Kernel compiled with retpoline option: UNKNOWN (couldn't read your kernel configuration)
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3'
* Kernel supports Page Table Isolation (PTI): NO
* PTI enabled and active: NO
* Reduced performance impact of PTI: NO (PCID/INVPCID not supported, performance impact of PTI will be significant)
* Running as a Xen PV DomU: NO
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3640 [rogue system register read] aka 'Variant 3a'
* CPU microcode mitigates the vulnerability: NO
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3639 [speculative store bypass] aka 'Variant 4'
* Kernel supports speculation store bypass: YES (found in /proc/self/status)
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3615/3620/3646 [L1 terminal fault] aka 'Foreshadow & Foreshadow-NG'
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
Need more detailed information about mitigation options? Use --explain
A false sense of security is worse than no security at all, see --disclaimer
● RASPBERRY PI CPU REVISION CODES
RASPBERRY PI REVISION CODES
cat /proc/cpuinfo
Hardware : BCM2835
Revision : a02082
Serial : 00000000765fc593
| Code | Model | Revision | RAM | Manufacturer |
| a22082 | 3B | 1.2 | 1 GB | Embest(China) |
| a32082 | 3B | 1.2 | 1 GB | Sony Japan |
| a52082 | 3B | 1.2 | 1 GB | Stadium(UK) |
| a020d3 | 3B+ | 1.3 | 1 GB | Sony UK |
・Raspberry Piで Spectreと Meltdownの CPUの脆弱性をチェックする方法

・Raspberry Piで Spectreと Meltdownの CPUの脆弱性をチェックする方法

Tags: [Raspberry Pi], [電子工作]
●関連するコンテンツ(この記事を読んだ人は、次の記事も読んでいます)

FWinSdCardImager SDカード イメージ書き込みアプリ、ラズパイの Raspbian OS、Jetson Nanoの Ubuntuの書き込みに便利
ラズパイや Jetson Nano等のワンボードマイコン等への OSイメージの書き込みが簡単にできる

FWinPiFinder ラズベリーパイ IPアドレス発見アプリ。ARPコマンドでラズパイの IPアドレスを探索発見する
Raspberry Piや NVIDIA Jetson Nano等の IPアドレスを MACアドレスの OUI部分を使用して発見する

Raspberry Pi 3系のトラブルであるある第一位の電源トラブル、低電圧警報に関する情報のまとめ
ラズパイ3B系での低電圧警報に関する情報まとめ、コマンドラインやログファイルから低電圧を検知する方法

Raspberry Pi Zero Wを海外通販の Pimoroni等での購入方法、購入できる通販ショップ一覧まとめ
ラズパイゼロW ワイヤレスモデルを海外通販でサクッと簡単に個人輸入で入手。技適通過でも国内販売は常に品切れ

Raspberry Pi 3で安定して使える相性の無い最適な microSDカードの種類のまとめ
ラズパイ3で安定して使える microSDカードを購入する Teamと SanDiskは絶対に買わない

Raspberry Pi 3 Model Bに専用カメラモジュール RaspiCamを接続する方法
ラズパイに専用カメラモジュールを接続して Raspbianで写真の静止画撮影や動画を録画する方法

Raspberry Pi 3の Linuxコンソール上で使用する各種コマンドまとめ
ラズパイの Raspbian OSのコマンドラインで使用する便利コマンド、負荷試験や CPUシリアル番号の確認方法等も

Raspberry Pi 3公式フォーラムの FAQの内容の日本語訳
ラズパイ公式フォーラムの「The Raspberry Pi 3 Model B Q&A thread」の日本語訳

Raspberry Pi 3で GPIO端子の I2C機能を有効化する方法
ラズパイ3の GPIO端子の I2C機能を有効にして各種センサーを繋げる方法まとめ

大人気の CPUボード、Raspberry Pi 3 Model Bで作ってみよう
Raspberry Piの開発環境の構築やタッチパネル付き液晶ディスプレイや各種センサーの使い方まとめ
 Raspberry Pi関連はこちらへまとめました
Raspberry Pi関連はこちらへまとめました
下記以外にも多数のラズパイ関係の記事が有ります。
(I2C制御、GPIO制御、1-Wire制御、シリアル通信、日本語音声合成、日本語音声認識、中国語音声合成、MeCab 形態素解析エンジン、赤外線リモコン制御、秋月 I2C液晶モジュール、KeDei 3.5インチ液晶、HDMI 5インチ液晶、NFCカードリーダ、コマンドライン操作方法等)

Espressif ESP8266 Arduino互換でスケッチが使える ESP-12Eモジュール基板
Espressif ESP8266 ESP-12-E NodeMCU V1 ESP12 CP2102

BangGood通販はドローン以外にも面白い商品がまだまだ有った(電子工作編)
レーザー彫刻機、カラー液晶の DIYオシロ、Arduinoや Raspberry Pi用の小型カラー液晶
[HOME]
|
[BACK]
リンクフリー(連絡不要、ただしトップページ以外は Web構成の変更で移動する場合があります)
Copyright (c)
2018 FREE WING,Y.Sakamoto
Powered by 猫屋敷工房 & HTML Generator
http://www.neko.ne.jp/~freewing/raspberry_pi/raspberry_pi_check_spectre_meltdown_vulnerable/